OWASP ZAP Zed Attack Proxy
my modifications to contribute to the community…
First of all I’d like to thank all members of the community who have contributed with this amazing project!
If you don’t know what is this project, you can check the official github.
This post will be focused to explain the modifications that I’ve done.
Motivation
I was using the zapproxy to test APIs, but in certain moments I felt difficulty to scan the APIs which needed of authentication.
I had 3 environments [‘Development’,’Homolog’,’Production’]. Then over a hundred APIs to test, most of them authenticated. So I decided to create some files and adapt my needs in a generic way, so that it could be used by other people.
zap_ConfigFile
This is the main file, which control all the things.
In this file I do some actions in this order:
- Set the environment variables
- Read all swaggers from the directory
- Call the authentication function
- Create the config file
- Start the container
zap_Auth
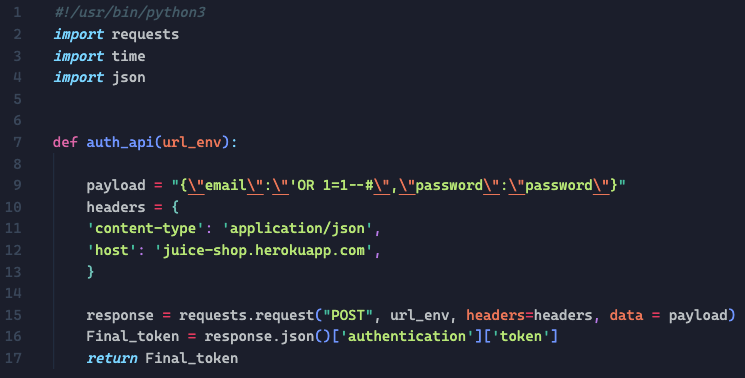
I’ve created an example content, using the Juice Shop as my target. This file is simple you just have to put code to authenticate into your target and then return the “Final_token”.
.prop file
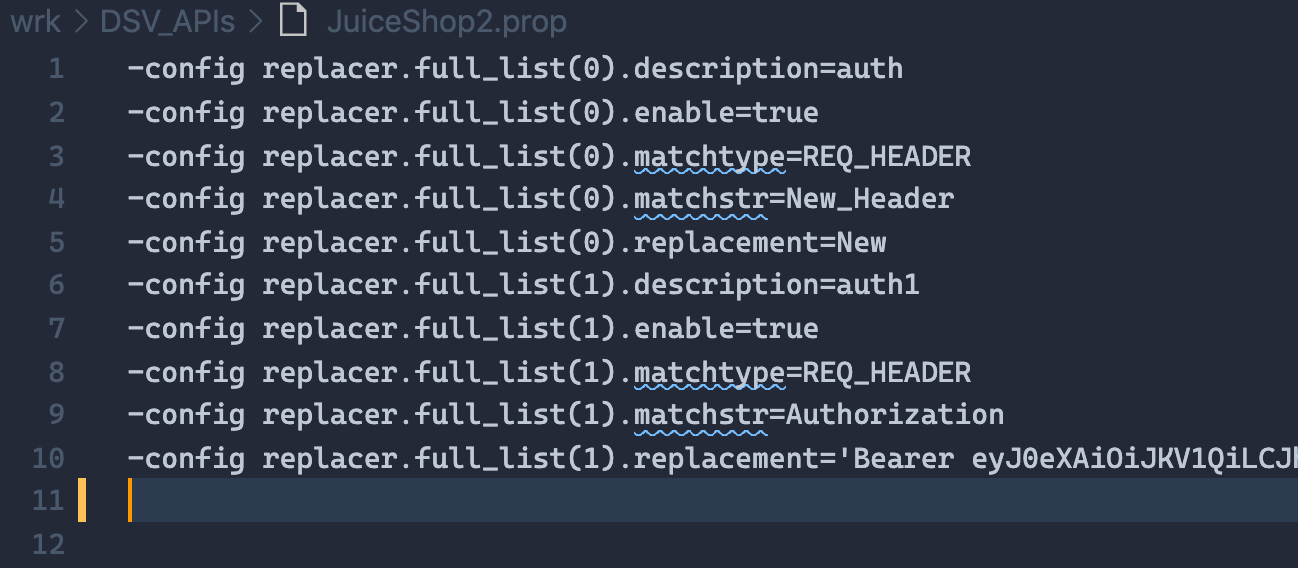
Now it’s time to create the swagger_Name.prop file, which will serve us as the config file containing all the Headers we want to. Including the token from the authentication, or even another value, you are free to add any new header and set up to your request.
zap_environment
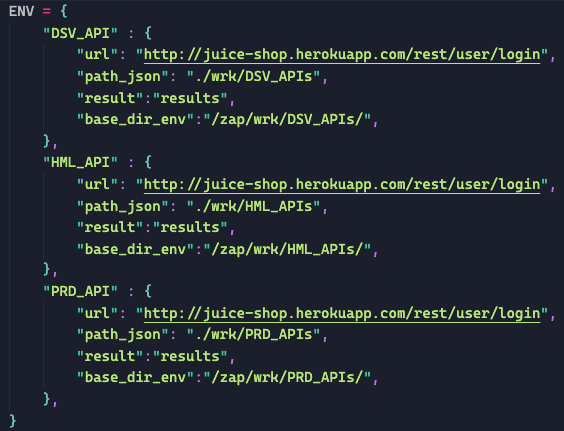
The environment is set, to identify which one you have chosen. And finally the container is called passing all the necessary arguments. But to get it working I had to modify the zap-api-scan.py and zap-common files.
Zap_api_scan
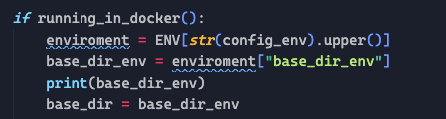
This is the core of the zapproxy API scan, so I did carefully changes.
- Added new option for the environment
"-e". - Changed the “hardcoded path”, to the new one coming from the environment file.
- Then passed the new base_dir variable to the add_zap_options function.
This function is called by:
zap-common
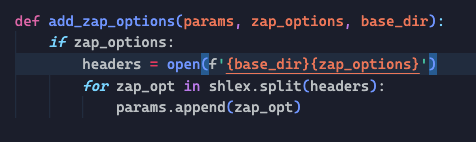
Basically this files is called by function add_zap_options, now can it read the .prop config file based on the environment and set it up to the scan. Instead of passing all the arguments inline.
Conclusion
Now you can have multiple environments with a lot of APIs with different authentications and you will be able to scan in a more assertive way.
Here is the Pull Request with all changes made.
Usage:
docker-compose up;
python3 zap_ConfigFile + environment [dsv_api, hml_api, prd_api]
Posts:
- Post Board parte 2
- Post Board parte 1
- Guess Me Parte 2
- Guess Me Parte 1
- Food Store
- IOT Connect
- UnCrackable L1 Parte 2
- UnCrackable L1 Parte 1
- CVE-2022-26352
- DCA php
- Docker Code Analyzer
- Vulnado Parte 3
- Vulnado Parte 2
- Vulnado Parte 1
- Damm Vulnerable WebSocket
- OWASP ZAP Zed Attack Proxy
- Estratégias de um code review
- O que é code review?